Discover expert articles, tutorials, and industry trends.
Tech Hub
Stay ahead of the curve with our cutting-edge insights and comprehensive resources.
Our Business is Good Tech
Technology is the foundation of our business.
We understand that exceptional technology is the key to delivering outstanding experiences for car buyers and retailers. That's why we constantly seek out the latest advancements, tools, and ideas that will shape the future of vehicle retailing.
We are committed to fostering an environment that cultivates innovation, inspires creativity, and encourages groundbreaking solutions. We believe in nurturing a culture where innovative thinking thrives, empowering our team to tackle challenges with fresh perspectives and develop new approaches that push the boundaries of what's possible.
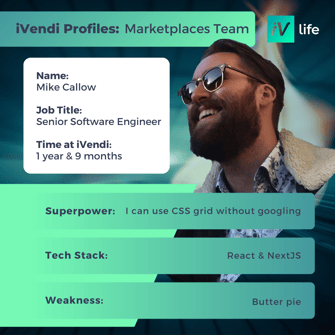
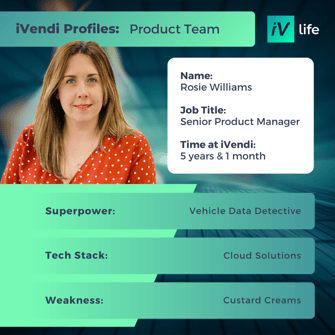
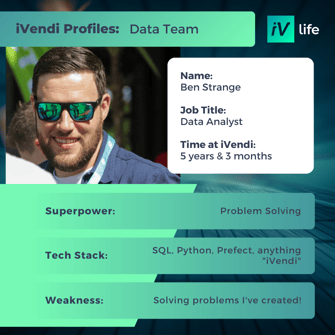
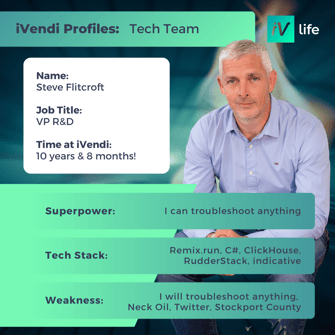
Meet our Tech Team
At iVendi innovation, expertise, and collaboration thrive.
Comprising a group of passionate and skilled professionals, our Tech Team is at the forefront of cutting-edge technologies and software development practices. With a shared dedication to excellence, we consistently deliver groundbreaking solutions that drive our company's success and empower our clients. Together, we tackle complex challenges, push boundaries, and transform ideas into reality.
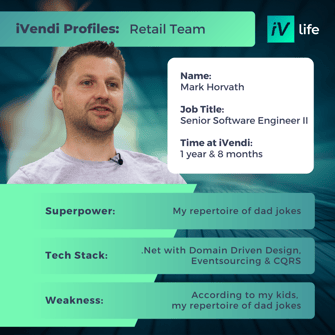
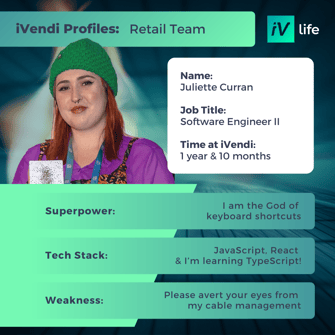
Get to know some of our Product & Tech all stars below:
Cybersecurity Checklist

There are times when the cyber threat to an organisation is greater than usual.
It has been reported that phishing attempts increased by as much as 300% in February 2022, so increased vigilance is clearly the order of the day.
91% of UK companies experienced at least one successful email-based phishing attack last year.
Organisations should consider, officially or unofficially, moving to a heightened state of alert.
Acknowledging the increased threat level can help prioritise necessary cybersecurity questions and give you the best chance of preventing a cyber-attack.
Being prepared will help you recover quickly if you become a victim.
In this post, we’ll provide a checklist that outlines ten steps an organisation can take when responding to a heightened cyber threat.
Why is cybersecurity important?
As our world becomes more reliant on digital tools, the number of factors influencing cybersecurity continues to increase.
More recently, the situation in Ukraine has caused an increased level of malicious activity, with a multi-market European motor retailer being targeted by the Hive ransomware group.
Internet giants Google have taken steps to bolster their own presence in the cybersecurity world, recently acquiring Mandiant, a frontline cyber threat intelligence group, for a sum of $5.4 Billion.
Simon Hunt, our Head of Information Security & Compliance, said: “It is widely acknowledged that we are currently seeing a substantially increased threat level and, only a few weeks ago, a general warning was issued by official cybersecurity bodies in the US, UK and Australia about high levels of activity.
“While details of the major European dealer group incident are limited, it illustrates how motor retailers – perhaps especially larger businesses – are potentially vulnerable to malicious attacks that could seriously compromise their ability to operate in the short term and damage their reputation in the longer term.
“What we can also say with some certainty from our wide experience of the dealer sector in the UK and across Europe is that security standards vary widely.”
Our 7 point security check
Check that your internet connection and patching are up-to-date
Check that records of your internet connections are up to date. This should include factors such as which IP addresses your systems use on the web and which domain names belong to your organisation.
Domain registration data should be held securely. Your domain registry account should have a strong password and MFA, if available.
Carry out an external vulnerability scan of all your internet connections and check that everything you need to patch has been patched.
Make sure your servers, PCs, laptops and mobile devices are patched and up to date. This should include all applications as well as OS and firmware. It’s a good idea to use a patch management solution and turn on automatic updates where possible.
Be sure that web-facing services are patched for known security vulnerabilities. Services of this type that remain unpatched can represent a very high risk and are likely to be targeted by attackers.
You should also check the business cases and mitigating factors for known unpatched systems in relation to the increased threat.
Check access controls, third party access and password policy
Make sure all users are using unique passwords which are not used on other, personal accounts. Ask users to check that their passwords are strong and get them to immediately change any which are not.
Password managers are an excellent way to maintain strong and unique passwords. If multi-factor authentication (MFA) is available, make sure it is enabled.
Be sure to review accounts that have privileged or administrative access and remove old, unused or unrecognised accounts. Privileged accounts could be system administrators, but could also be accounts that have access to sensitive systems or information.
If you need to let third party organisations have access to your systems, make sure you have a clear understanding of what level of privilege is extended into your systems, and who controls it.
During a time of increased cyber risk, you should be sure to remove any access that is no longer required.
Before allowing connection, you should review the security practices of the third parties in question. Supply chain attacks have been a rapidly increasing threat vector in recent times.
Following the principle of ‘least privilege’ is the best policy when managing access controls.
Check your defences
Ensure antivirus software is installed on all PCs and laptops, and regularly check that it is active on all systems and that signatures are up-to-date.
Recheck that your firewall rules are as you would expect. In particular, you should check for temporary rules that may have been left in place beyond their expected use.
Check logging and monitoring
Review the logging you have in place. Check how logs are protected and how long they are retained. They should be held for a minimum of one month.
For the period of increased risk, you should consider increasing the frequency with which you check security logs on servers and network devices. A log management solution or SIEM will help a great deal with this process.
Check your backup and recovery strategy
Confirm that your backups are running correctly and that you have a documented recovery plan. Check that a recovery test has been carried out recently so that you can be confident you will recover from a system loss.
Recovery tests are important as they often reveal incorrect assumptions about how recovery from backup will work. The recovery test should additionally check that critical dependencies, other than data, can also be recovered, such as private keys and access tokens.
Check your phishing response capability and incident response plan
Educating users on how to recognise likely phishing attempts and other forms of social engineering should be a part of your security awareness training plan.
Make sure that staff know how to report phishing emails and that you have a process in place to deal with any security incidents that are reported.
Review your incident response plan and check it is up-to-date. Double check that escalation plans and corresponding contact details are all correct.
Make sure it is clear who has the authority to make key decisions both during and outside of normal business hours if these individuals are different.
Your incident response plan should be available to all who may need it, whether they are in the office or working remotely.
Check sources of threat intelligence
Staying up to date with relevant threats during a period of increased cyber risk is critical to avoiding and responding to security risks.
There are many excellent sources of threat intelligence, but a good default source is the National Cyber Security Centre (NCSC) website.
You can go further and sign up for an NCSC CiSP account, through which you can access and share information about threats with other organisations, as well as receiving immediate updates.
It is also possible to register for the NCSC Early Warning Service so that the organisation can inform you of any malicious activity originating from your systems.
More from iVendi
iVendi Life
We like to celebrate success, learn from each other, and have fun along the way.